Revealing huge surveillance programme risks damaging US national security, James Clapper says
Disclosure of the massive surveillance of phone records and internet communications risks “long-lasting and irreversible harm” to US national security, the director of national intelligence says.
Late on Thursday night US time James Clapper issued a bullet-point defence of the surveillance programs disclosed by the Guardian and the Washington Post, saying they contained “numerous safeguards that protect privacy and civil liberties”. To correct the “misleading impression left in the article” – apparently a reference to the Guardian’s original story – Clapper said he approved the declassification of his defence of the National Security Agency’s collection of every phone record from millions of Verizon customers.
“There is a robust legal regime in place governing all activities conducted pursuant to the Foreign Intelligence Surveillance Act,” Clapper wrote, “which ensures that those activities comply with the Constitution and laws and appropriately protect privacy and civil liberties. The program at issue here is conducted under authority granted by Congress and is authorized by the Foreign Intelligence Surveillance Court (FISC). By statute, the Court is empowered to determine the legality of the program.”
Clapper attacked the disclosures by the Guardian and the Washington Post as “reprehensible” for risking “important protections for the security of Americans”.
A judge for Fisa Court, as the surveillance body is known, reviewed and approved the surveillance. But critics have pointed out that the Fisa Court has almost never, in its 35-year history, rejected a US surveillance request – a perception of docility that prompted its presiding judge, Reggie Walton, to defend the court’s integrity in a statement to the Guardian on Thursday.
Clapper said the Fisa Court had established procedures preventing the government “indiscriminately sifting” through the collected phone records. “The court only allows the data to be queried when there is a reasonable suspicion, based on specific facts, that the particular basis for the query is associated with a foreign terrorist organisation,” Clapper said. “Only a small fraction of the records are ever reviewed” by “specifically cleared counterterrorism personnel”.
At the same time, Clapper said national security required the NSA to collect all the Verizon subscriber data, even if not all the data would be analysed, and regardless of any evidence to link the phone records to crime, foreign espionage or terrorism. On Thursday, the Wall Street Journal reported that other telecoms received similar orders from the government for the subscriber data.
“The collection is broad in scope,” Clapper wrote, “because more narrow collection would limit our ability to protect the nation from terrorist threats to the United States, as it may assist counterterrorism personnel to discover whether known or suspected terrorists have been in contact with other persons who may be engaged in terrorist activities.”
Yet the collection does not need to be tied to terrorism to occur – something that alarmed one Democrat senator, Jeff Merkley. He told the Guardian on Thursday that the sweeping “barn-door” collection appeared to violate the provision of the Patriot Act purportedly authorising it.
“We can’t really propose changes to the law unless we know what the words mean as interpreted by the court,” Merkley said.
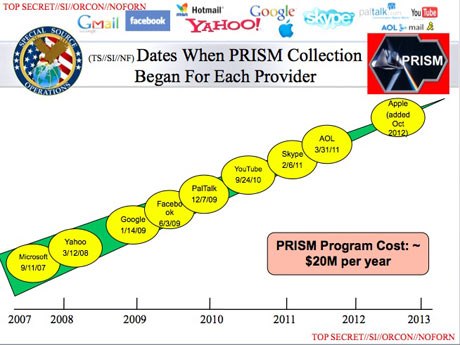
Clapper reiterated a point the Obama administration made on Thursday in its response to the Guardian’s story: the NSA’s dragnet of Verizon phone records, which the Fisa Court authorised until 19 July, does not include the “content of any communications or the identity of any subscriber”. Yet the so-called “metadata” – phone numbers, duration of calls – can be combined with publicly available information to easily determine subscriber identity. And a second NSA surveillance effort, disclosed by the Guardian on Thursday and codenamed PRISM, collects the content of communications provided through Google, Facebook, Microsoft, Apple and five other large internet companies.
Clapper came under criticism on Thursday for statements to Democrat senator Ron Wyden that appeared to be contradicted by the revelations of the surveillance programs. Asked in March whether “millions” of Americans had “any kind of [their] data” collected by the US government, Clapper replied: “Not wittingly. There are cases where they could inadvertently perhaps collect, but not wittingly.”
He has denied misleading Congress, but Clapper’s statement on Thursday suggested the collection of Americans’ phone records was deliberate, methodical and institutionalised.
“Discussing programs like this publicly,” Clapper concluded, “will have an impact on the behavior of our adversaries and make it more difficult for us to understand their intentions.”
http://www.guardian.co.uk/world/2013/jun/07/us-tech-nsa-data-clapper
President Obama’s Dragnet
By THE EDITORIAL BOARD
Within hours of the disclosure that federal authorities routinely collect data on phone calls Americans make, regardless of whether they have any bearing on a counterterrorism investigation, the Obama administration issued the same platitude it has offered every time President Obama has been caught overreaching in the use of his powers: Terrorists are a real menace and you should just trust us to deal with them because we have internal mechanisms (that we are not going to tell you about) to make sure we do not violate your rights.
Those reassurances have never been persuasive — whether on secret warrants to scoop up a news agency’s phone records or secret orders to kill an American suspected of terrorism — especially coming from a president who once promised transparency and accountability.
The administration has now lost all credibility on this issue. Mr. Obama is proving the truism that the executive branch will use any power it is given and very likely abuse it. That is one reason we have long argued that the Patriot Act, enacted in the heat of fear after the Sept. 11, 2001, attacks by members of Congress who mostly had not even read it, was reckless in its assignment of unnecessary and overbroad surveillance powers.
Based on an article in The Guardian published Wednesday night, we now know that the Federal Bureau of Investigation and the National Security Agency used the Patriot Act to obtain a secret warrant to compel Verizon’s business services division to turn over data on every single call that went through its system. We know that this particular order was a routine extension of surveillance that has been going on for years, and it seems very likely that it extends beyond Verizon’s business division. There is every reason to believe the federal government has been collecting every bit of information about every American’s phone calls except the words actually exchanged in those calls.
Articles in The Washington Post and The Guardian described a process by which the N.S.A. is also able to capture Internet communications directly from the servers of nine leading American companies. The articles raised questions about whether the N.S.A. separated foreign communications from domestic ones.
A senior administration official quoted in The Times online Thursday afternoon about the Verizon order offered the lame observation that the information does not include the name of any caller, as though there would be the slightest difficulty in matching numbers to names. He said the information “has been a critical tool in protecting the nation from terrorist threats,” because it allows the government “to discover whether known or suspected terrorists have been in contact with other persons who may be engaged in terrorist activities, particularly people located inside the United States.”
That is a vital goal, but how is it served by collecting everyone’s call data? The government can easily collect phone records (including the actual content of those calls) on “known or suspected terrorists” without logging every call made. In fact, the Foreign Intelligence Surveillance Act was expanded in 2008 for that very purpose.
Essentially, the administration is saying that without any individual suspicion of wrongdoing, the government is allowed to know whom Americans are calling every time they make a phone call, for how long they talk and from where.
This sort of tracking can reveal a lot of personal and intimate information about an individual. To casually permit this surveillance — with the American public having no idea that the executive branch is now exercising this power — fundamentally shifts power between the individual and the state, and it repudiates constitutional principles governing search, seizure and privacy.
The defense of this practice offered by Senator Dianne Feinstein of California, who as chairwoman of the Senate Intelligence Committee is supposed to be preventing this sort of overreaching, was absurd. She said on Thursday that the authorities need this information in case someone might become a terrorist in the future. Senator Saxby Chambliss of Georgia, the vice chairman of the committee, said the surveillance has “proved meritorious, because we have gathered significant information on bad guys and only on bad guys over the years.”But what assurance do we have of that, especially since Ms. Feinstein went on to say that she actually did not know how the data being collected was used?
The senior administration official quoted in The Times said the executive branch internally reviews surveillance programs to ensure that they “comply with the Constitution and laws of the United States and appropriately protect privacy and civil liberties.”
That’s no longer good enough. Mr. Obama clearly had no intention of revealing this eavesdropping, just as he would not have acknowledged the killing of Anwar al-Awlaki, an American citizen, had it not been reported in the press. Even then, it took him more than a year and a half to acknowledge the killing, and he is still keeping secret the protocol by which he makes such decisions.
We are not questioning the legality under the Patriot Act of the court order disclosed by The Guardian. But we strongly object to using that power in this manner. It is the very sort of thing against which Mr. Obama once railed, when he said in 2007 that the surveillance policy of the George W. Bush administration “puts forward a false choice between the liberties we cherish and the security we provide.”
Two Democrats on the Senate Intelligence Committee, Ron Wyden of Oregon and Mark Udall of Colorado, have raised warnings about the government’s overbroad interpretation of its surveillance powers. “We believe most Americans would be stunned to learn the details of how these secret court opinions have interpreted Section 215 of the Patriot Act,” they wrote last year in a letter to Attorney General Eric Holder Jr. “As we see it, there is now a significant gap between what most Americans think the law allows and what the government secretly claims the law allows. This is a problem, because it is impossible to have an informed public debate about what the law should say when the public doesn’t know what its government thinks the law says.”
On Thursday, Representative Jim Sensenbrenner, Republican of Wisconsin, who introduced the Patriot Act in 2001, said that the National Security Agency overstepped its bounds by obtaining a secret order to collect phone log records from millions of Americans.
“As the author of the Patriot Act, I am extremely troubled by the F.B.I.’s interpretation of this legislation,” he said in a statement. “While I believe the Patriot Act appropriately balanced national security concerns and civil rights, I have always worried about potential abuses.” He added: “Seizing phone records of millions of innocent people is excessive and un-American.”
Stunning use of the act shows, once again, why it needs to be sharply curtailed if not repealed.
http://www.nytimes.com/2013/06/07/opinion/president-obamas-dragnet.html?pagewanted=2&_r=0
FISA: A Law With Many Loopholes
By Jacob Gershman
To find the legal authority underpinning the top-secret Prism surveillance program, we once again turn to the Foreign Intelligence Surveillance Act.
Law Blog on Thursday wrote about the statute allowing the government to compel the production of “business records” relevant to a foreign intelligence probe.
Another statute, Section 702 of FISA, provides procedures for spying on the online communication of foreigners or groups located outside our borders.
In a statement Thursday, Director of National Intelligence James R. Clapper said Section 702 “cannot be used to intentionally target any U.S. citizen, any other U.S. person, or anyone located within the United States.”
But the statute passed by Congress in 2008 leaves quite a bit of wiggle room, according to legal experts. Here are some potential loopholes:
‘Reasonably believed’: The Attorney General and the intelligence director must certify to a special surveillance judge that targets are “reasonably believed to be located outside the United States.” How certain is that? According to the Washington Post, that means a 51% confidence, similar to the preponderance of evidence standard.
“Given the scale of collection here, even if [the error rate] were only a few percent, we’d still be talking about a huge number of American communications,” Julian Sanchez, a research fellow at the Cato Institute, told Law Blog.
Also, the government doesn’t have to be 51% sure that the target isn’t an American citizen nor a legal resident. The government just has to assert that it’s not intentionally targeting a citizen or legal resident.
Who’s the target? There’s another ambiguity around the notion of a target. It’s unclear whether NSA interprets the law to allow the government to tap into accounts belonging to Americans as long as the surveillance is broadly directed at a foreign group, like Al Qaeda, according to Mr. Sanchez.
Optional verifying: The targeting procedures are subject to judicial review by the Foreign Intelligence Surveillance Court, but “the court is not required to look behind the assertions made in the certifications” submitted by the attorney and the national intelligence director, according to an analysis of the law prepared by the Congressional Research Service, a nonpartisan and independent group that advises Congress on legal matters.
Exigent circumstances: In the absence of a court order, the attorney general and intelligence director may also authorize targeting if they determine that “exigent circumstances exist which would cause the loss or delay of important national security intelligence, according to the Congressional Research Service. The government has seven days to submit the “certification” paperwork to the court, but it can move forward with the spying during that week.
“They’re assuring us that there are secret procedures in place to protect privacy, but there’s never been a public evaluation of them,” Michelle Richardson, legislative counsel for the American Civil Liberties Union’s Washington Legislative Office, told Law Blog. “We’re disinclined to take their word for it knowing that they are doing things like collecting everybody’s telephone records.”
Mr. Clapper in his statement said that information collected under Prism “is among the most important and valuable foreign intelligence information we collect, and is used to protect our nation from a wide variety of threats.”
Mr. Clapper also said in his statement that “activities authorized” by the law “involve extensive procedures . . . to ensure that only non-U.S. persons outside the U.S. are targeted . . . ”
A spokesperson for Mr. Clapper’s office did not immediately respond to a request seeking comment.
http://blogs.wsj.com/law/2013/06/07/fisa-a-law-with-many-loopholes/
Background Articles and Videos
Foreign Intelligence Surveillance Act (FISA)
The Foreign Intelligence Surveillance Act of 1978 (“FISA” Pub.L. 95–511, 92 Stat. 1783, 50 U.S.C. ch. 36) is a United States law which prescribes procedures for the physical and electronic surveillance and collection of “foreign intelligence information” between “foreign powers” and “agents of foreign powers” (which may include American citizens and permanent residents suspected of espionage or terrorism).[1] The law does not apply outside the United States. The law has been repeatedly amended since the September 11 attacks.
Subsequent amendments
The Act was amended in 2001 by the USA PATRIOT Act, primarily to include terrorism on behalf of groups that are not specifically backed by a foreign government.
An overhaul of the bill, the Protect America Act of 2007 was signed into law on August 5, 2007.[2] It expired on February 17, 2008.
The FISA Amendments Act of 2008 passed by the United States Congress on July 9, 2008.[3]
History
The Foreign Intelligence Surveillance Act (FISA) was introduced on May 18, 1977, by Senator Ted Kennedy and was signed into law by President Carter in 1978. The bill was cosponsored by the nine Senators: Birch Bayh, James O. Eastland, Jake Garn, Walter Huddleston, Daniel Inouye, Charles Mathias, John L. McClellan, Gaylord Nelson, and Strom Thurmond.
The FISA resulted from extensive investigations by Senate Committees into the legality of domestic intelligence activities. These investigations were led separately by Sam Ervin and Frank Church in 1978 as a response to President Richard Nixon’s usage of federal resources to spy on political and activist groups, which violates the Fourth Amendment.[4] The act was created to provide Judicial and congressional oversight of the government’s covert surveillance activities of foreign entities and individuals in the United States, while maintaining the secrecy needed to protect national security. It allowed surveillance, without court order, within the United States for up to one year unless the “surveillance will acquire the contents of any communication to which a United States person is a party”. If a United States person is involved, judicial authorization was required within 72 hours after surveillance begins.
Bush administration warrantless domestic wiretapping program
The Act came into public prominence in December 2005 following publication by the New York Times of an article[5] that described a program of warrantless domestic wiretapping ordered by the Bush administration and carried out by the National Security Agency since 2002; a subsequent Bloomberg article[6] suggested that this may have already begun by June 2000.
Scope and limits
For most purposes, including electronic surveillance and physical searches, “foreign powers” means a foreign government, any faction(s) or foreign governments not substantially composed of U.S. persons, and any entity directed or controlled by a foreign government. §§1801(a)(1)-(3) The definition also includes groups engaged in international terrorism and foreign political organizations. §§1801(a)(4) and (5). The sections of FISA authorizing electronic surveillance and physical searches without a court order specifically exclude their application to groups engaged in international terrorism. See §1802(a)(1) (referring specifically to §1801(a)(1), (2), and (3)).
The statute includes limits on how it may be applied to U.S. persons. A “U.S. person” includes citizens, lawfully admitted permanent resident aliens, and corporations incorporated in the United States.
The code defines “foreign intelligence information” to mean information necessary to protect the United States against actual or potential grave attack, sabotage or international terrorism.[7]
In sum, a significant purpose of the electronic surveillance must be to obtain intelligence in the United States on foreign powers (such as enemy agents or spies) or individuals connected to international terrorist groups. To use FISA, the government must show probable cause that the “target of the surveillance is a foreign power or agent of a foreign power.”[4][8]
Provisions
The subchapters of FISA provide for:
The act created a court which meets in secret, and approves or denies requests for search warrants. Only the number of warrants applied for, issued and denied, is reported. In 1980 (the first full year after its inception), it approved 322 warrants.[9] This number has steadily grown to 2,224 warrants in 2006.[10] In the period 1979-2006 a total of 22,990 applications for warrants were made to the Court of which 22,985 were approved (sometimes with modifications; or with the splitting up, or combining together, of warrants for legal purposes), and only 5 were definitively rejected.[11]
Electronic surveillance
Generally, the statute permits electronic surveillance in two scenarios.
Without a court order
The President may authorize, through the Attorney General, electronic surveillance without a court order for the period of one year provided it is only for foreign intelligence information;[7] targeting foreign powers as defined by 50 U.S.C. § 1801(a)(1),(2),(3)[12] or their agents; and there is no substantial likelihood that the surveillance will acquire the contents of any communication to which a United States person is a party.[13]
The Attorney General is required to make a certification of these conditions under seal to the Foreign Intelligence Surveillance Court,[14] and report on their compliance to the House Permanent Select Committee on Intelligence and the Senate Select Committee on Intelligence.[15]
Since 50 U.S.C. § 1802(a)(1)(A) of this act specifically limits warrantless surveillance to foreign powers as defined by 50 U.S.C. §1801(a) (1),(2), (3) and omits the definitions contained in 50 U.S.C. §1801(a) (4),(5),(6) the act does not authorize the use of warrantless surveillance on: groups engaged in international terrorism or activities in preparation therefore; foreign-based political organizations, not substantially composed of United States persons; or entities that are directed and controlled by a foreign government or governments.[16] Under the FISA act, anyone who engages in electronic surveillance except as authorized by statute is subject to both criminal penalties[17] and civil liabilities.[18]
Under 50 U.S.C. § 1811, the President may also authorize warrantless surveillance at the beginning of a war. Specifically, he may authorize such surveillance “for a period not to exceed fifteen calendar days following a declaration of war by the Congress”.[19]
With a court order
Alternatively, the government may seek a court order permitting the surveillance using the FISA court.[20] Approval of a FISA application requires the court find probable cause that the target of the surveillance be a “foreign power” or an “agent of a foreign power”, and that the places at which surveillance is requested is used or will be used by that foreign power or its agent. In addition, the court must find that the proposed surveillance meet certain “minimization requirements” for information pertaining to U.S. persons.[21]
Physical searches
In addition to electronic surveillance, FISA permits the “physical search” of the “premises, information, material, or property used exclusively by” a foreign power. The requirements and procedures are nearly identical to those for electronic surveillance.
FISA court
The Act created the Foreign Intelligence Surveillance Court (FISC) and enabled it to oversee requests for surveillance warrants by federal police agencies (primarily the F.B.I.) against suspected foreign intelligence agents inside the U.S. The court is located within the Department of Justice headquarters building. The court is staffed by eleven judges appointed by the Chief Justice of the United States to serve seven year terms.
Proceedings before the FISA court are ex parte and non-adversarial. The court hears evidence presented solely by the Department of Justice. There is no provision for a release of information regarding such hearings, or for the record of information actually collected.
Denials of FISA applications by the FISC may be appealed to the Foreign Intelligence Surveillance Court of Review. The Court of Review is a three judge panel. Since its creation, the court has come into session twice: in 2002 and 2008.
Remedies for violations
Both the subchapters covering physical searches and electronic surveillance provide for criminal and civil liability for violations of FISA.
Criminal sanctions follows violations of electronic surveillance by intentionally engaging in electronic surveillance under the color of law or through disclosing information known to have been obtained through unauthorized surveillance. The penalties for either act are fines up to $10,000, up to five years in jail, or both.[17]
In addition, the statute creates a cause of action for private individuals whose communications were unlawfully monitored. The statute permits actual damages of not less than $1,000 or $100 per day. In addition, that statute authorizes punitive damages and an award of attorney’s fees.[18] Similar liability is found under the subchapter pertaining to physical searches. In both cases, the statute creates an affirmative defense for a law enforcement agent acting within their official duties and pursuant to a valid court order. Presumably, such a defense is not available to those operating exclusively under presidential authorization.
Lone wolf amendment
In 2004 FISA was amended to include a “lone wolf” provision. 50 U.S.C. § 1801(b)(1)(C). A “lone wolf” is a non-U.S. person who engages in or prepares for international terrorism. The provision amended the definition of “foreign power” to permit the FISA courts to issue surveillance and physical search orders without having to find a connection between the “lone wolf” and a foreign government or terrorist group. However, “if the court authorizes such a surveillance or physical search using this new definition of ‘agent of a foreign power’, the FISC judge has to find, in pertinent part, that, based upon the information provided by the applicant for the order, the target had engaged in or was engaging in international terrorism or activities in preparation therefor”.[22]
Constitutionality
Before FISA
In 1967 the Supreme Court of the United States held that the requirements of the Fourth Amendment applied equally to electronic surveillance and to physical searches. Katz v. United States, 389 U.S. 347 (1967). The Court did not address whether such requirements apply to issues of national security. Shortly after, in 1972, the Court took up the issue again in United States v. United States District Court, Plamondon, where the court held that court approval was required in order for the domestic surveillance to satisfy the Fourth Amendment. 407 U.S. 297 (1972). Justice Powell wrote that the decision did not address this issue that “may be involved with respect to activities of foreign powers or their agents”.
In the time immediately preceding FISA, a number of courts squarely addressed the issue of “warrantless wiretaps”. In both United States v. Brown, 484 F.2d 418 (5th Cir. 1973), and United States v. Butenko, 494 F.2d 593 (3rd Cir. 1974), the courts upheld warrantless wiretaps. In Brown, a U.S. citizen’s conversation was captured by a wiretap authorized by the Attorney General for foreign intelligence purposes. In Butenko, the court held a wiretap valid if the primary purpose was for gathering foreign intelligence information.
A plurality opinion in Zweibon v. Mitchell, 516 F.2d 594 (D.C. Cir. 1975), held that a warrant was required for the domestic surveillance of a domestic organization. In this case, the court found that the domestic organization was not a “foreign power or their agent”, and “absent exigent circumstances, all warrantless electronic surveillance is unreasonable and therefore unconstitutional.”
Post-FISA
There have been very few cases involving the constitutionality of FISA. In two lower court decisions, the courts found FISA constitutional. In the United States v. Duggan, the defendants were members of the Irish Republican Army. 743 F.2d 59 (2nd Cir., 1984). They were convicted for various violations regarding the shipment of explosives and firearms. The court held that there were compelling considerations of national security in the distinction between the treatment of U.S. citizens and non-resident aliens.
In the United States v. Nicholson, the defendant moved to suppress all evidence gathered under a FISA order. 955 F.Supp. 588 (Va. 1997). The court affirmed the denial of the motion. There the court flatly rejected claims that FISA violated Due process clause of the Fifth Amendment, Equal protection, Separation of powers, nor the Right to counsel provided by the Sixth Amendment.
However, in a third case, the special review court for FISA, the equivalent of a Circuit Court Of Appeals, opined differently should FISA limit the President’s inherent authority for warrantless searches in the foreign intelligence area. In In re Sealed Case, 310 F.3d 717, 742 (Foreign Intel. Surv. Ct. of Rev. 2002) the special court stated “[A]ll the other courts to have decided the issue [have] held that the President did have inherent authority to conduct warrantless searches to obtain foreign intelligence information . . . . We take for granted that the President does have that authority and, assuming that is so, FISA could not encroach on the President’s constitutional power.”
Criticisms
K. A. Taipale of the World Policy Institute, James Jay Carafano of the Heritage Foundation,[23] and Philip Bobbitt of Columbia Law School,[24] among others,[25] have argued that FISA may need to be amended (to include, among other things, procedures for programmatic approvals) as it may no longer be adequate to address certain foreign intelligence needs and technology developments, including: the transition from circuit-based communications to packet-based communications; the globalization of communications infrastructure; and the development of automated monitoring techniques, including data mining and traffic analysis.[26]
The need for programmatic approval of technology-enabled surveillance programs is particularly crucial in foreign intelligence. See, for example, John R. Schmidt, the associate attorney general (1994–1997) in the Justice Department under President Bill Clinton,[27] recalling early arguments made by then-Attorney General Edward Levi to the Church Committee that foreign intelligence surveillance legislation should include provisions for programmatically authorizing surveillance programs because of the particular needs of foreign intelligence where “virtually continuous surveillance, which by its nature does not have specifically predetermined targets” may be required. In these situations, “the efficiency of a warrant requirement would be minimal.”
And, in a recent essay, Judge Richard A. Posner opined that FISA “retains value as a framework for monitoring the communications of known terrorists, but it is hopeless as a framework for detecting terrorists. [FISA] requires that surveillance be conducted pursuant to warrants based on probable cause to believe that the target of surveillance is a terrorist, when the desperate need is to find out who is a terrorist.”[28]
Amendments
Terrorist Surveillance Act of 2006
On March 16, 2006, Senators Mike DeWine (R-OH), Lindsey Graham (R-SC), Chuck Hagel (R-NE), and Olympia Snowe (R-ME) introduced the Terrorist Surveillance Act of 2006 (S.2455),[29][30] under which the President would be given certain additional limited statutory authority to conduct electronic surveillance of suspected terrorists in the United States subject to enhanced Congressional oversight. Also on March 16, 2006, Senator Arlen Specter (R-PA) introduced the National Security Surveillance Act of 2006 (S. 2453),[31][32] which would amend FISA to grant retroactive amnesty[33] for warrantless surveillance conducted under presidential authority and provide FISA court (FISC) jurisdiction to review, authorize, and oversight “electronic surveillance programs”. On May 24, 2006, Senator Specter and Senator Dianne Feinstein (D-CA) introduced the Foreign Intelligence Surveillance Improvement and Enhancement Act of 2006 (S. 3001) asserting FISA as the exclusive means to conduct foreign intelligence surveillance.
All three competing bills were the subject of Judiciary Committee hearings throughout the summer.[34] On September 13, 2006, the Senate Judiciary Committee voted to approve all three mutually exclusive bills, thus, leaving it to the full Senate to resolve.[35]
On July 18, 2006, U.S. Representative Heather Wilson (R-NM) introduced the Electronic Surveillance Modernization Act (H.R. 5825). Wilson’s bill would give the President the authority to authorize electronic surveillance of international phone calls and e-mail linked specifically to identified terrorist groups immediately following or in anticipation of an armed or terrorist attack on the United States. Surveillance beyond the initial authorized period would require a FISA warrant or a presidential certification to Congress. On September 28, 2006 the House of Representatives passed Wilson’s bill and it was referred to the Senate.[36]
Protect America Act of 2007
On July 28, 2007, President Bush called on Congress to pass legislation to reform the FISA in order to ease restrictions on surveillance of terrorist suspects where one party (or both parties) to the communication are located overseas. He asked that Congress pass the legislation before its August 2007 recess. On August 3, 2007, the Senate passed a Republican-sponsored version of FISA (S. 1927) in a vote of 60 to 28. The House followed by passing the bill, 227–183. The Protect America Act of 2007 (Pub.L. 110–55, S. 1927) was then signed into law by George W. Bush on 2007-08-05.[37]
Under the Protect America Act of 2007, communications that begin or end in a foreign country may be wiretapped by the U.S. government without supervision by the FISA Court. The Act removes from the definition of “electronic surveillance” in FISA any surveillance directed at a person reasonably believed to be located outside the United States. As such, surveillance of these communications no longer requires a government application to, and order issuing from, the FISA Court.
The Act provides procedures for the government to “certify” the legality of an acquisition program, for the government to issue directives to providers to provide data or assistance under a particular program, and for the government and recipient of a directive to seek from the FISA Court, respectively, an order to compel provider compliance or relief from an unlawful directive. Providers receive costs and full immunity from civil suits for compliance with any directives issued pursuant to the Act.
A summary of key provisions follows. The Act empowers the Attorney General or Director of National Intelligence (“DNI”) to authorize, for up to one year, the acquisition of communications concerning “persons reasonably believed to be outside the United States” if the Attorney General and DNI determine that each of five criteria has been met:
- There are reasonable procedures in place for determining that the acquisition concerns persons reasonably believed to be located outside the United States;
- The acquisition does not constitute electronic surveillance (meaning it does not involve solely domestic communications);
- The acquisition involves obtaining the communications data from or with the assistance of a communications service provider who has access to communications;
- A significant purpose of the acquisition is to obtain foreign intelligence information; and
- Minimization procedures outlined in the FISA will be used.
This determination by the Attorney General and DNI must be certified in writing, under oath, and supported by appropriate affidavit(s). If immediate action by the government is required and time does not permit the preparation of a certification, the Attorney General or DNI can direct the acquisition orally, with a certification to follow within 72 hours. The certification is then filed with the FISA Court.
Once the certification is filed with the FISA Court, the Attorney General or DNI can direct a provider to undertake or assist in the undertaking of the acquisition.
If a provider fails to comply with a directive issued by the Attorney General or DNI, the Attorney General may seek an order from the FISA Court compelling compliance with the directive. Failure to obey an order of the FISA Court may be punished as a contempt of court.
Likewise, a person receiving a directive may challenge the legality of that directive by filing a petition with the FISA Court. An initial review must be conducted within 48 hours of the filing to determine whether the petition is frivolous, and a final determination concerning any non-frivolous petitions must be made – in writing – within 72 hours of receipt of the petition.
Determinations of the FISA Court may be appealed to the Foreign Intelligence Court of Appeals, and a petition for a writ of certiorari of a decision from the FICA can be made to the U.S. Supreme Court.
All petitions must be filed under seal.
The Act allows providers to be compensated, at the prevailing rate, for providing assistance as directed by the Attorney General or DNI.
The Act provides explicit immunity from civil suit in any federal or state court for providing any information, facilities, or assistance in accordance with a directive under the Act.
Within 120 days, the Attorney General must submit to the FISA Court for its approval the procedures by which the government will determine that acquisitions authorized by the Act conform with the Act and do not involve purely domestic communications. The FISA Court then will determine whether the procedures comply with the Act. The FISA Court thereafter will enter an order either approving the procedures or directing the government to submit new procedures within 30 days or cease any acquisitions under the government procedures. The government may appeal a ruling of the FISA Court to the FICA and ultimately the Supreme Court.
On a semiannual basis, the Attorney General shall inform the Intelligence and Judiciary Committees of the House and Senate of incidents of noncompliance with a directive issued by the Attorney General or the DNI, incidents of noncompliance with FISA Court-approved procedures by the Intelligence Community, and the number of certifications and directives issued during the reporting period.
The amendments to FISA made by the Act expire 180 days after enactment, except that any order in effect on the date of enactment remains in effect until the date of expiration of such order and such orders can be reauthorized by the FISA Court.”[38] The Act expired on February 17, 2008.
Subsequent developments
Legal experts experienced in national security issues are divided on how broadly the new law could be interpreted or applied. Some believe that due to subtle changes in the definitions of terms such as “electronic surveillance”, it could empower the government to conduct warrantless physical searches and even seizures of communications and computer devices and their data which belong to U.S. citizens while they are in the United States, if the government contended that those searches and potential seizures were related to its surveillance of parties outside the United States. Intelligence officials, while declining to comment directly on such possibilities, respond that such interpretations are overly broad readings of the act, and unlikely to actually occur. Democratic lawmakers have nonetheless indicated that they are planning to introduce a revised version of the legislation for consideration as early as September 2007.[39]
In a September 10, 2007 address at a symposium on modernizing FISA held at Georgetown University Law Center‘s National Security Center, Kenneth L. Wainstein, Assistant Attorney General for National Security, argued against the current six-month sunset provision in the Protect America Act of 2007, saying that the broadened surveillance powers the act provides for should be made permanent. Wainstein proposed that internal audits by the Office of the Director of National Intelligence and the National Security Division of the Justice Department, with reporting to select groups of Congressmen, would ensure that the expanded capability would not be abused.[40]
Also on September 10, DNI Mike McConnell testified before the Senate Committee on Homeland Security and Governmental Affairs that the Protect America Act had helped foil a major terror plot in Germany. U.S. intelligence-community officials questioned the accuracy of McConnell’s testimony and urged his office to correct it, which he did in a statement issued September 12, 2007. Critics cited the incident as an example of the Bush administration’s exaggerated claims and contradictory statements about surveillance activities. Counterterrorism officials familiar with the background of McConnell’s testimony said they did not believe he made inaccurate statements intentionally as part of any strategy by the administration to persuade Congress to make the new eavesdropping law permanent. Those officials said they believed McConnell gave the wrong answer because he was overwhelmed with information and merely mixed up his facts.[41]
Speaking at National Security Agency headquarters in Fort Meade, Maryland on September 19, 2007, President George W. Bush urged Congress to make the provisions of the Protect America Act permanent. Bush also called for retroactive immunity for telecommunications companies who had cooperated with government surveillance efforts, saying, “It’s particularly important for Congress to provide meaningful liability protection to those companies now facing multibillion-dollar lawsuits only because they are believed to have assisted in efforts to defend our nation, following the 9/11 attacks”.[42]
On October 4, 2007, the bipartisan Liberty and Security Committee of the Constitution Project, co-chaired by David Keene and David D. Cole, issued its “Statement on the Protect America Act”.[43] The Statement urged Congress not to reauthorize the PAA, saying the language of the bill “runs contrary to the tripartite balance of power the Framers envisioned for our constitutional democracy, and poses a serious threat to the very notion of government of the people, by the people and for the people”. Some in the legal community have questioned the constitutionality of any legislation that would retroactively immunize telecommunications firms alleged to have cooperated with the government from civil liability for having potentially violated their customers’ privacy rights.[44]
In an article appearing in the January/February 2008 issue of the Institute of Electrical and Electronics Engineers journal of Security and Privacy, noted technology experts from academia and the computing industry found significant flaws in the technical implementation of the Protect America Act which they said created serious security risks, including the danger that such a surveillance system could be exploited by unauthorized users, criminally misused by trusted insiders, or abused by the government.[45]
On October 7, 2007, the Washington Post reported that House Democrats planned to introduce alternative legislation which would provide for one-year “umbrella” warrants, and would require the Justice Department inspector general to audit the use of those warrants and issue quarterly reports to a special FISA court and to Congress. The proposed bill would not include immunity for telecommunications firms facing lawsuits in connection with the administration’s NSA warrantless surveillance program. House Democrats said that as long as the administration withholds requested documents explaining the basis for the program that they cannot consider immunity for firms alleged to have facilitated it.[46] On October 10, 2007 comments on the White House South Lawn, President Bush said he would not sign any bill that did not provide retroactive immunity for telecommunications corporations.[47]
On October 18, 2007, the House Democratic leadership put off a vote on the proposed legislation by the full chamber to avoid consideration of a Republican measure that made specific references to Osama bin Laden. At the same time, the Senate Intelligence Committee reportedly reached a compromise with the White House on a different proposal that would give telephone carriers legal immunity for any role they played in the National Security Agency’s domestic eavesdropping program approved by President Bush after the Sept. 11 terrorist attacks.[48]
On November 15, 2007, the Senate Judiciary Committee voted 10-9 along party lines to send an alternative measure to the full Senate other than the one the intelligence committee had crafted with the White House. The proposal would leave to the full Senate whether or not to provide retroactive immunity to telecommunications firms that cooperated with the NSA. Judiciary Committee chairman Patrick Leahy said that granting such immunity would give the Bush administration a “blank check” to do what it wants without regard to the law. Arlen Specter of Pennsylvania, the top Republican on the committee, said that court cases may be the only way Congress can learn exactly how far outside the law the administration has gone in eavesdropping in the United States. When the full Senate takes up the bill, Specter is expected to offer a compromise that would shield the companies from financial ruin but allow lawsuits to go forward by having the federal government stand in for the companies at trial.[49]
On the same day, the House of Representatives voted 227-189 to approve a Democratic bill that would expand court oversight of government surveillance inside the United States while denying immunity to telecom companies. House Judiciary Committee chairman John Conyers left the door open to an immunity deal in the future, but said that the White House must first give Congress access to classified documents specifying what the companies did that requires legal immunity.[50]
 |
Wikisource has original text related to this article: |






You must be logged in to post a comment.